-
What Is DLP (Data Loss Prevention)? | Guide to DLP Security
- Why is DLP important?
- What is data loss?
- Understanding data leaks
- What are the different types of data loss?
- What are the different types of data threats?
- What is data leakage prevention?
- What is a data loss prevention policy?
- How does DLP work?
- What is data loss prevention software?
- What are the components of a data loss solution?
- What are the different types of DLP solutions?
- What are the benefits of DLP solutions?
- What are the challenges associated with DLP solutions?
- What are the primary DLP use cases?
- How to successfully adopt and deploy DLP in 7 steps
- What is DLP’s role in compliance?
- 2024 data loss prevention statistics
- 2024 data loss prevention trends
- Top 10 DLP best practices, tips, and tricks
- DLP FAQs
- Data Loss Prevention – Protecting Your Sensitive Enterprise Data
- What Is Data Loss Prevention (DLP) Compliance?
What Is Cloud Data Loss Prevention (DLP)?
Cloud data loss prevention (DLP) is a data security strategy that proactively monitors, detects, and prevents sensitive data exposure or exfiltration within cloud environments. Advanced DLP solutions employ techniques such as data classification, pattern matching, and machine learning to accurately identify and safeguard critical information. By enforcing context-aware policies, DLP ensures compliance with regulatory standards and mitigates the risk of data breaches in complex cloud-based infrastructures.
Cloud Data Loss Prevention (DLP) Explained
Cloud data loss prevention (DLP) refers to a set of solutions that ensure the protection of sensitive data within an organization’s cloud storage from being misused or leaked. Traditional data loss prevention solutions differ in that they're typically deployed on-premises and focus on protecting an organization's endpoints and internal network infrastructure.
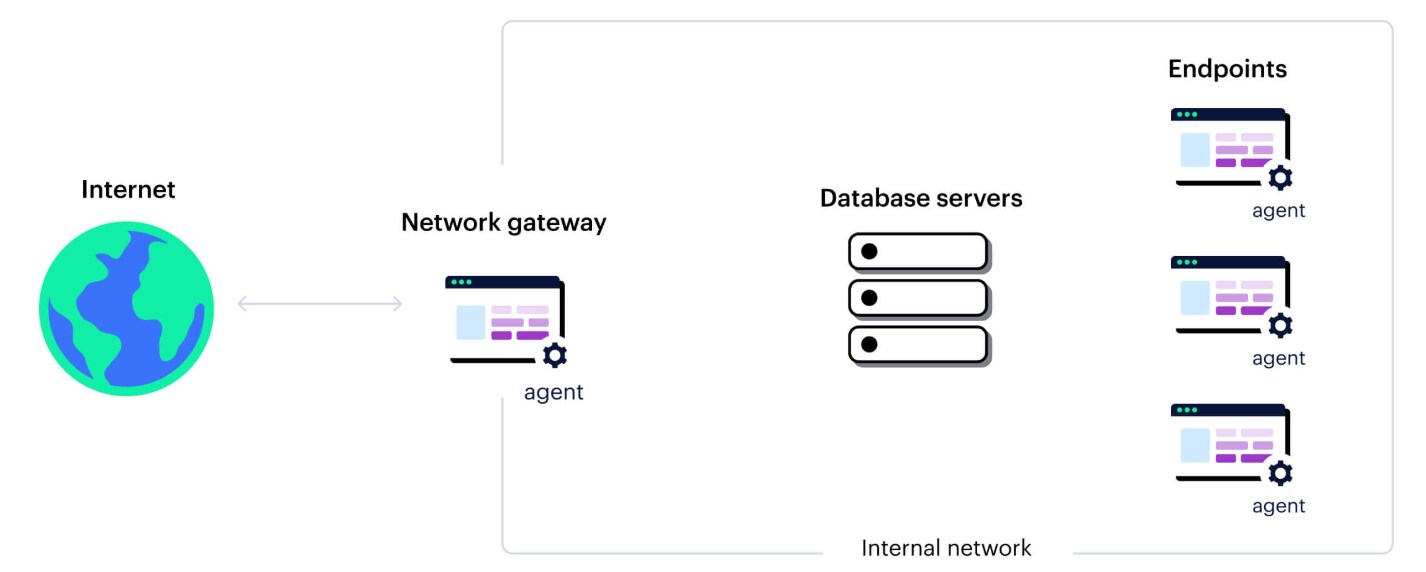
Figure 1: Traditional approaches to DLP were developed for the old perimeter — when organizations stored data on their physical server infrastructure, and data movement was restricted to internal networks.
A primary use case for cloud DLP solutions was accelerated when employees transitioned into a hybrid WFH model. Seemingly overnight, data usage went from traditional on-premises setups to the cloud. And not surprisingly, the rapid shift increased the risk of data breaches, particularly due to the heavy reliance on cloud-based collaboration platforms that open doors to new data exposures.
Sensitive Data in the Cloud
Sensitive data, such as personally identifiable information (PII), financial records, or intellectual property, are found in 66% of storage buckets and 63% of publicly exposed storage buckets, Unit 42® research recently showed. Both insider and external threats put this sensitive information at risk. The lack of insight into what type of information, such as PII or credit card numbers, is stored in each data object makes it difficult to protect sensitive information from accidental leakage. Research from the 2023 Data Breach Investigations Report puts risk in perspective, with 5,199 data breaches confirmed in 16,312 examined incidents.
How Cloud DLP Works
Cloud DLP works by leveraging best practices and advanced cloud data security techniques to minimize data at risk within cloud environments.
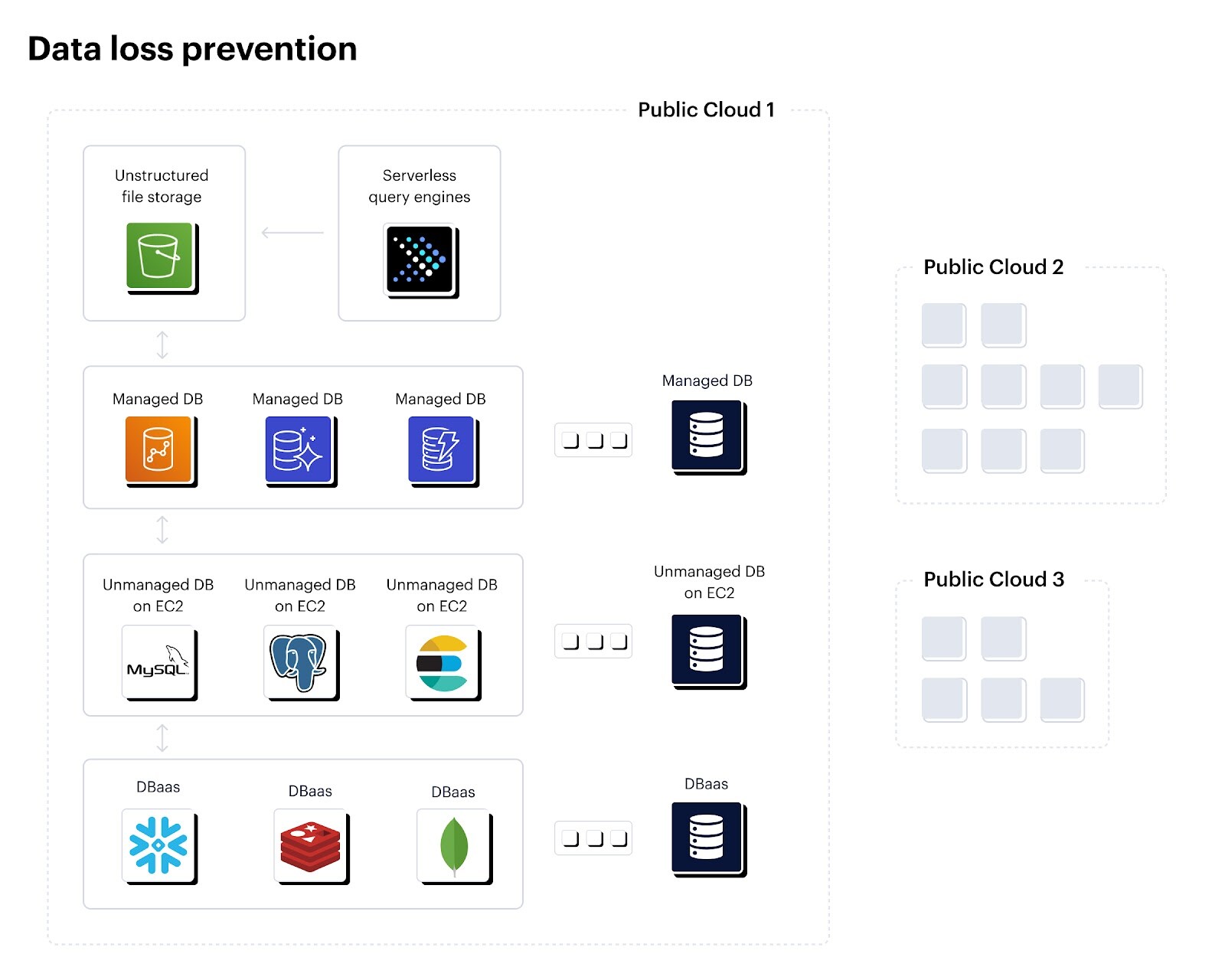
Figure 2: Balancing scalability and agility with data loss prevention in the public cloud
Data Discovery
Cloud DLP starts by scanning the organization's cloud infrastructure, including cloud storage services, databases, and applications. It looks for sensitive data such as personal information, financial records, intellectual property, or any other data defined by predefined policies that can cause a breach.
Data Classification
Once sensitive data is discovered, it's then classified into different categories based on predefined rules and policies. Data classification further breaks down the data by types that include public, internal, confidential, and restricted, being the most sensitive, typically involving trade secrets or financial transaction history.
Policy Enforcement
If a potential policy violation is discovered, the cloud DLP solution takes action based on predefined policies. These policies might include blocking data transmission, encrypting data, or applying data masking to prevent unauthorized access.
Continuous Monitoring and Detection
Finally, the cloud DLP continuously monitors data in transit and at rest within the cloud environment. It also scans for anomalies and suspicious behaviors that indicate potential security risks, such as data exfiltration attempts or unusual movement.
Traditional DLP Vs. Cloud DLP
Here’s a side-by-side comparison of how traditional DLP tools stack up against its counterpart in the cloud.
| Traditional DLP (The Old Way) | Cloud DLP (The New Way) |
| Struggle to provide comprehensive visibility into data flowing within cloud environments | Designed to seamlessly integrate with various cloud platforms, applications, and services with more enhanced visibility |
| Requires complex and time-consuming manual configuration efforts to implement and maintain | Simple to deploy and built with pre-configured policies and templates tailored for popular cloud services |
| Can’t inspect the content within encrypted files | Supports data encryption at rest and in transit |
| Can’t effectively detect insider threats or accidental data exposure | Can easily identify potential insider threats earlier through suspicious user behavior and anomaly detection capabilities |
| Can’t scale when handling large volumes of data | Designed to scale and handle the increased volume of data flow |
| Falls short when adapting to evolving data policy regulations | Easily updates to comply with changing data protection laws and policy regulations |
Benefits of Cloud DLP
The adoption of tighter access security controls and cloud DLP solutions has emerged as a cornerstone of security measures for fast-scaling enterprises.
Shadow IT Discovery
Cloud DLP helps identify unauthorized or unmanaged cloud applications, which is particularly important for employees unaware of an organization's IT policies or if proper security controls aren’t in place.
Enhanced Data Visibility
Cloud DLP enhances data discovery and classification capabilities, enabling IT teams to gain valuable insights into their data landscape. It does this by quickly identifying any sensitive data, understanding data flows, and prioritizing data protection efforts based on severity risk factors.
Streamline Regulatory Compliance
Regulatory compliance fines are expensive. GDPR violations, for example, can cost a company up to €20 million or 4% of worldwide turnover. Cloud DLP enforces encryption policies for sensitive data at rest and in transit, adding an extra layer of protection to meet compliance requirements. It also helps identify and classify sensitive data, implement data handling policies, and generate audit trails.
Provide a Security Shield Against Cloud Misconfigurations
Cloud DLP solutions can assess the security configurations of cloud services and applications almost instantly. It looks for common misconfigurations such as excessive permissions, disabling of logging and monitoring settings, and exposed storage access in public cloud containers such as S3 buckets.
Cloud Data Loss Prevention FAQ
Data breach prevention encompasses the strategies, processes, and technologies employed to protect sensitive information from unauthorized access, disclosure, or theft. Effective data breach prevention requires a layered security approach that includes network, application, and data-level protection measures.
Key aspects of data breach prevention include access controls, data encryption, intrusion detection and prevention systems, continuous monitoring, and timely security updates.
Data access governance refers to the systematic management of access controls, permissions, and policies for sensitive data within an organization. By implementing a centralized and granular approach, organizations can monitor and regulate user access, ensuring that only authorized users can access, modify, or share critical information.
Data access governance plays a pivotal role in mitigating insider threats, enhancing data security, and adhering to regulatory compliance requirements. Key components of data access governance include identity and access management, role-based access controls, and continuous auditing and monitoring of user activities.
Data privacy compliance refers to an organization's adherence to laws, regulations, and industry standards governing the collection, storage, processing, and sharing of personal and sensitive data.
Compliance requirements vary depending on the jurisdiction, sector, and type of data involved, with examples including the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and California Consumer Privacy Act (CCPA).
To achieve data privacy compliance, organizations must implement stringent data protection measures, respect individual privacy rights, and maintain transparency in their data handling practices. Regular audits, employee training, and incident response plans help to prevent and mitigate data privacy compliance violations.
Data security risk assessment is a systematic process of identifying, evaluating, and prioritizing potential risks to an organization's sensitive data. The assessment aims to uncover vulnerabilities and weaknesses in the data protection infrastructure, enabling organizations to implement appropriate safeguards and mitigate threats.
Steps in a data security risk assessment include defining the scope, identifying assets, determining threats and vulnerabilities, evaluating the impact of potential risks, and prioritizing remediation efforts.