Cloud Posture Security, Cloud Security, Data Security Posture Management, DSPM
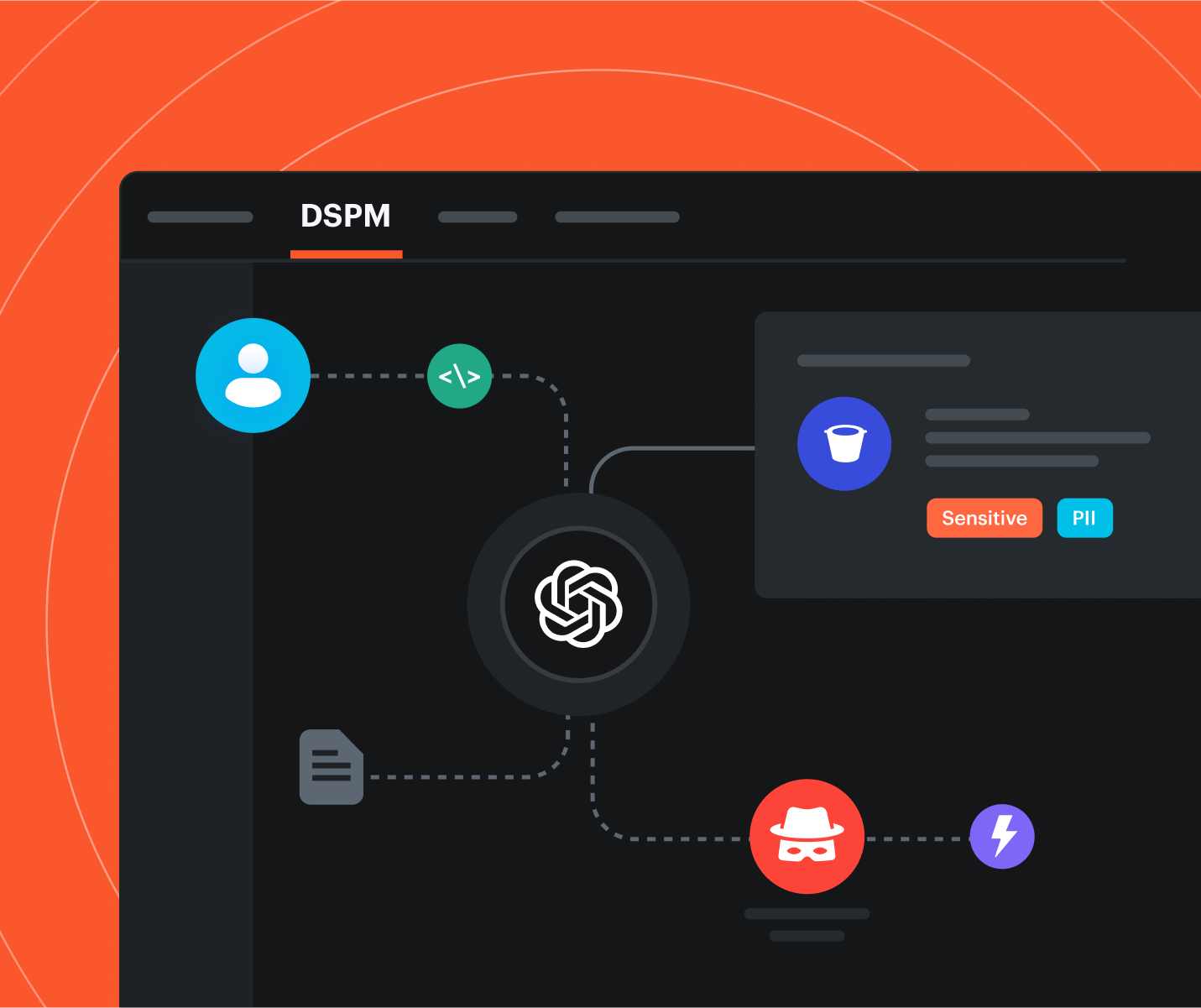
Weak Identity Governance Leads to Data Exposure — 3 Attack Paths Explained...
Cloud identity security depends on more than IAM hygiene. Learn how attackers exploit data access paths—and how to stop them with unified security intelligence.