Introduction
Threat actors frequently use the Tor network to anonymize their malicious activities, including unauthorized access attempts. While legitimate users may also use Tor for privacy reasons, successful logins originating from Tor exit nodes often require immediate scrutiny due to their potential association with account compromise attempts.
The A Successful Login from Tor playbook in the Cortex XSIAM’s Response and Remediation Pack automates the detection and remediation process for such logins, providing security teams with a structured approach to investigating suspicious authentication activities.
Threat Overview
Threat actors exploit Tor exit nodes to:
- Bypass security controls and evade geo-based restrictions.
- Conduct credential stuffing and brute-force attacks.
- Launch account takeover attempts without revealing their real location.
- Circumvent monitoring tools that rely on IP-based anomaly detection.
This playbook triggers when a successful authentication event is detected from a Tor exit node, ensuring that security teams can respond swiftly and effectively.
Purpose of the Playbook
The A Successful Login from Tor playbook streamlines security responses by executing a structured sequence of actions to assess the risk, gather intelligence, and mitigate potential threats.
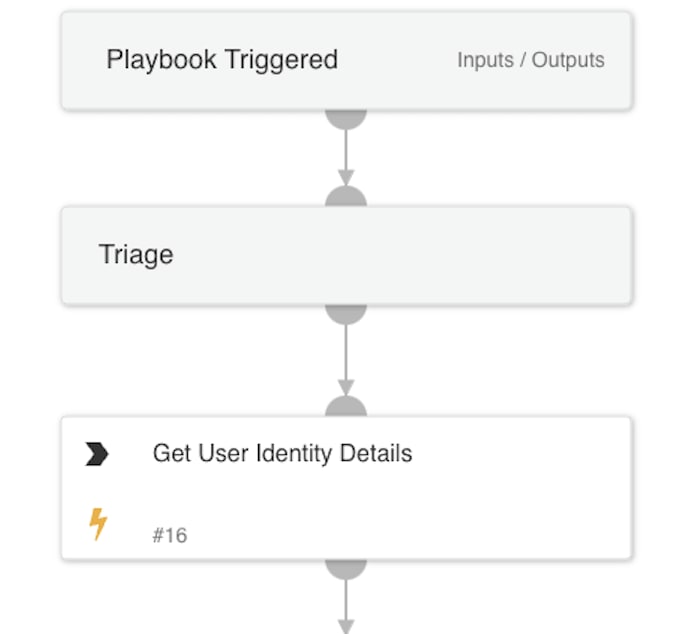
1. Triage
- Retrieves the user identity details to determine if the login is expected or anomalous.
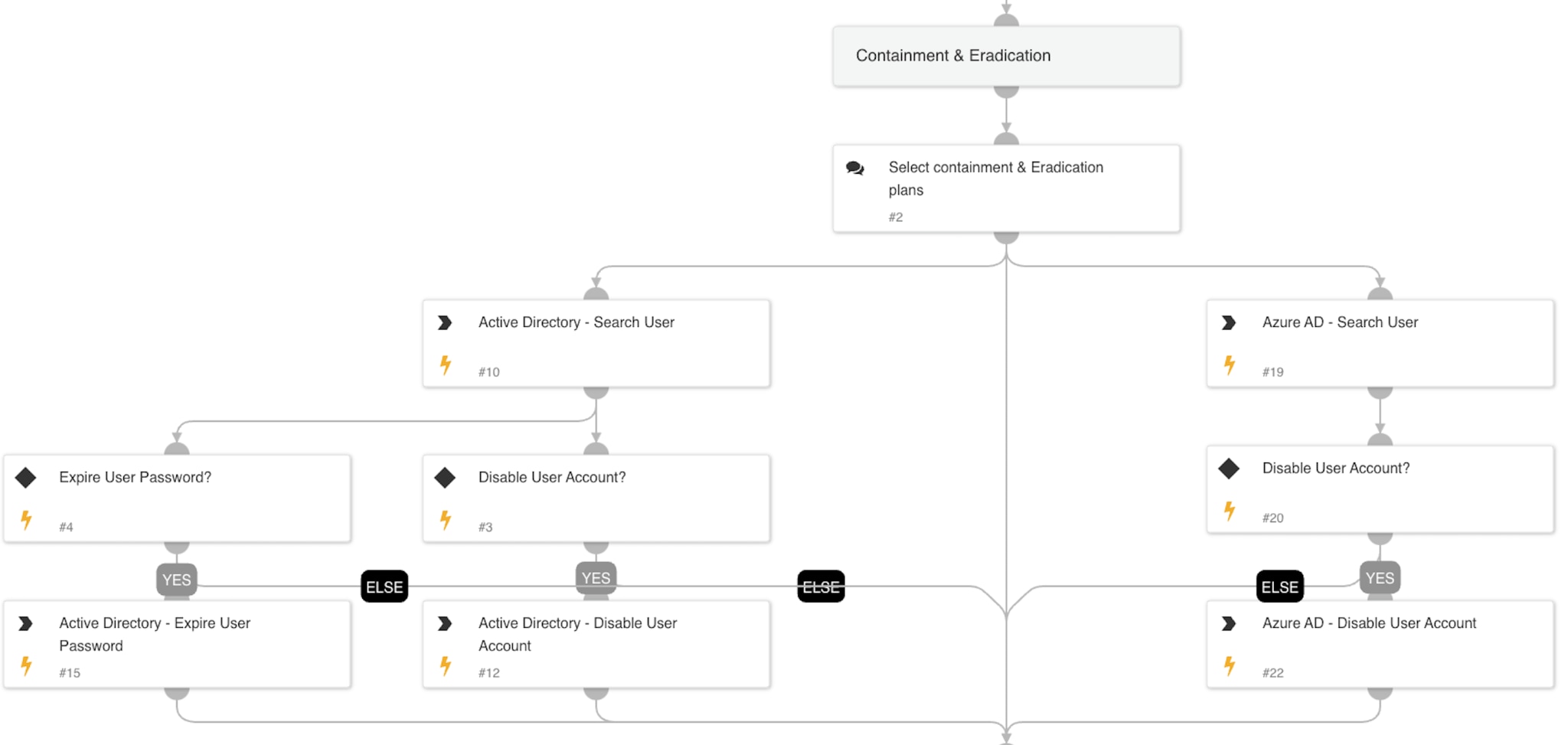
2. Remediation & Eradication
The playbook provides the security analyst with multiple remediation options, including:
- Disabling the user account via Active Directory or Azure AD.
- Expiring the user's password to force a reset and prevent further unauthorized access.
- Blocking traffic from Tor exit nodes using Palo Alto Networks PAN-OS and predefined External Dynamic Lists (EDL).
Security analysts can select one or multiple actions, and the playbook will execute them accordingly.
Integration Requirements
To leverage the full capabilities of this playbook, organizations need:
- Azure Active Directory (AD) Users or Active Directory Users for user identity management.
- PAN-OS Firewall with Cortex XSIAM integration to enforce network-level blocks.
Conclusion
The "A Successful Login from Tor" playbook in Cortex XSIAM enhances security teams’ ability to detect and respond to unauthorized access attempts using Tor. By automating identity verification, automated remediation, and network-level defenses, this playbook ensures rapid containment of potential threats.
For organizations looking to enhance their autonomous SOC capabilities, deploying this playbook can significantly improve security posture. Visit the Cortex XSIAM Response and Remediation Pack to learn more.
To learn more about how you can transform your SOC through automation, schedule a personal demo for Cortex XSIAM.